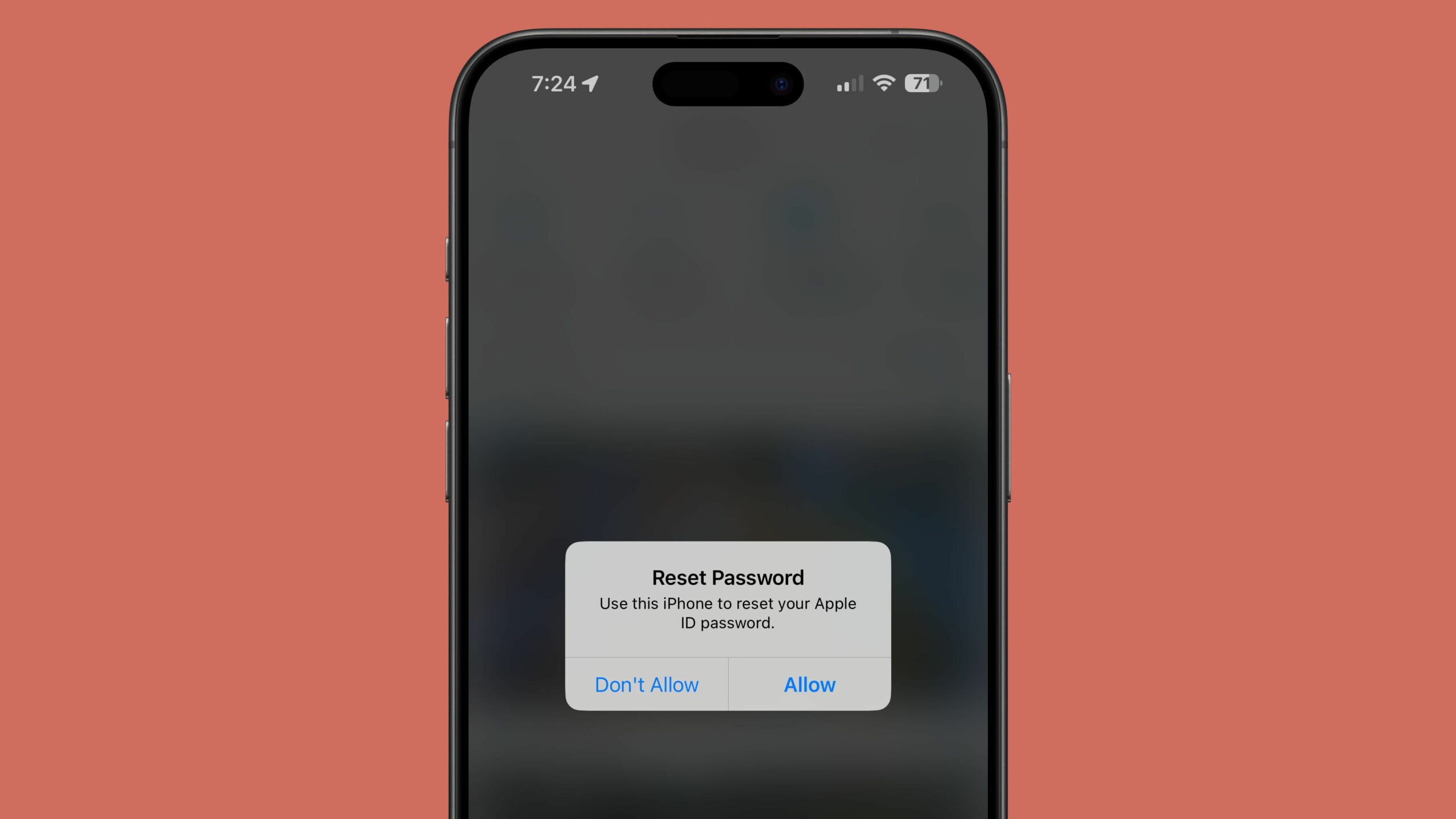
Phishing attacks exploiting a potential Apple password reset feature bug are on the rise, as reported by KrebsOnSecurity. Numerous Apple users have been targeted in these attacks, bombarded with relentless notifications or multi-factor authentication (MFA) messages to approve an Apple ID password change.
An attacker can manipulate the target’s iPhone, Apple Watch, or Mac to repeatedly display system-level password change approval texts, hoping the target will inadvertently approve the request or give in to the constant notifications by clicking the accept button. If approved, the attacker can change the Apple ID password and lock the user out of their account.
These password change requests affect all of the user’s devices, rendering them unusable until each popup is dismissed individually. One victim, Parth Patel, shared his ordeal of facing over 100 notifications before he could regain control of his devices. When targets resist clicking “Allow,” attackers resort to phony Apple-spoofed phone calls, seeking the one-time password sent during a password change attempt.
In Patel’s case, the attacker exploited leaked information from a people search website, utilizing his personal details to access his account. However, the attacker’s error in Patel’s name and suspicion-raising request for a one-time code exposed the scam. The success of this phishing attack relies on the attacker having access to the victim’s email address and phone number linked to their Apple ID.
Investigations by KrebsOnSecurity reveal that attackers exploit Apple’s forgotten Apple ID password page, bypassing the rate limit to flood users with malicious requests. Apple device owners should consistently reject all requests and be cautious of fraudulent phone calls requesting one-time password reset codes, as Apple does not follow such practices.
 Loading...
Loading...